Possible (and common) answers include:
- “I did not know there was access.”
- “That access should not have happened.”
- “It was a misconfiguration.”
- “The vulnerability was never patched. It was a Zero-day.”
These IAM mistakes are common, and now, cloud native practices bring several orders of magnitude of complexity that make IAM exploitation a clear and present danger. To prevent this, we recommend you answer these five questions to give your cloud security teams the visibility and data necessary to avoid these mistakes. Each question may not be simple to answer, but each are critical to assess your true cloud data risk exposure.
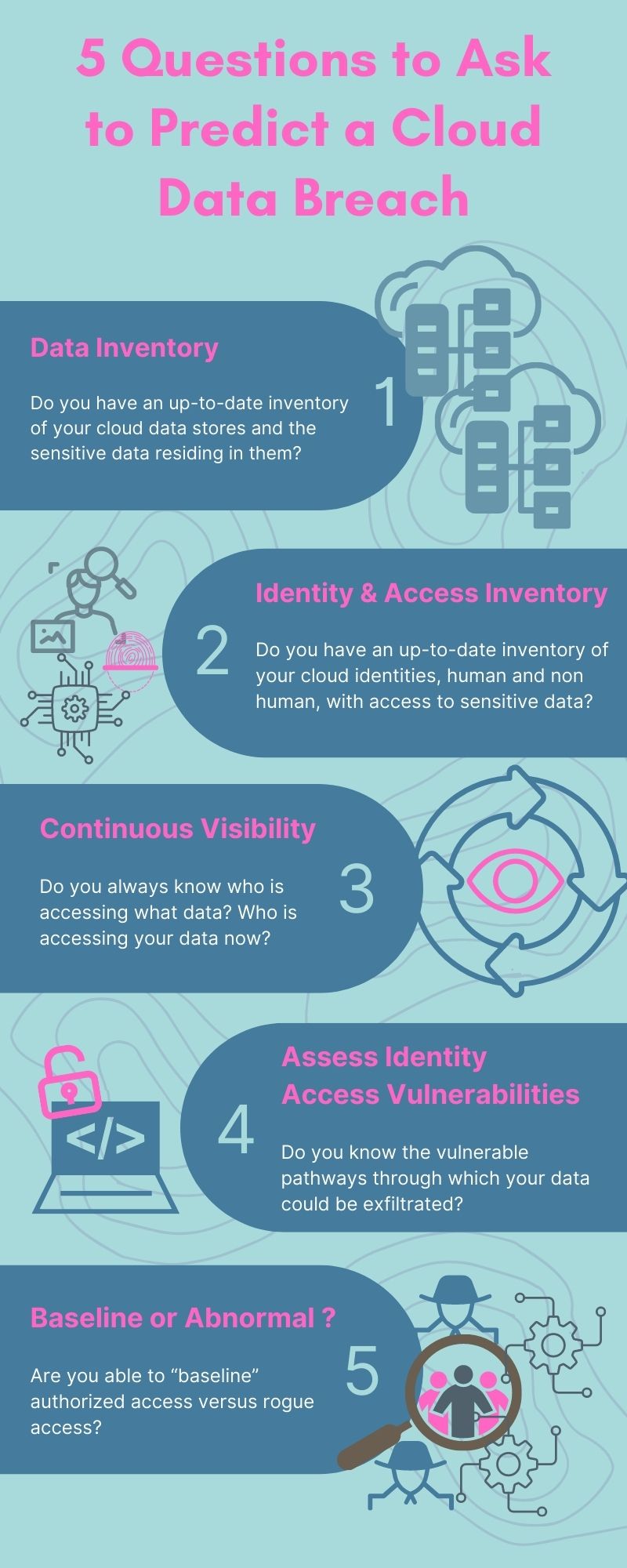
Five questions to understand your current cloud data posture and risk profile
- Do you have an up-to-date inventory of your cloud data stores and the sensitive data residing in them? (Data Inventory)
- Do you have an up-to-date inventory of your cloud identities, human and non human, with access to sensitive data? (Identity and Access Inventory)
- Do you always know who is accessing what data? Who is accessing your data now? (Continuous Visibility)
- Do you know the vulnerable pathways through which your data could be exfiltrated? (Assess Identity Access Vulnerabilities)
- Are you able to baseline authorized access versus rogue access? (Baseline vs Abnormal))
Determining where your sensitive data exists in the cloud is the very first step necessary to protect your data (Question 1: “Do you have an up-to-date inventory of your cloud data stores and the sensitive data residing in them?”). Without this, it is impossible for cloud security teams to take any preventative measures.
Once you have determined where your sensitive data lives, you can take the next step to investigate which identities exist in your cloud infrastructure (Question 2: “Do you have an up-to-date inventory of your cloud identities, human and non human, with access to sensitive data?”). The most difficult aspect of this is the ability to dynamically inventory the identities with access to your data. Human identities are relatively easily managed, IAM products and best practices enable this. However, non-human identities, such as those generated by APIs to automatically access resources are generating tens of thousands of access credentials at any point in time making it impossible to manually create an accurate inventory of identities with data access.
However, it’s not just the inventory of the datastores and identities that are key to preventing cloud data breaches. These two inventories are necessary prerequisites to answer Question 3 – “Do you always know who is accessing what data?”. For an honest view of your cloud data identity risks, it is necessary to know who is accessing what data – at all times. This starts by determining “Who’s got access to what?”. Another layer of complexity are the policy controls that manage data access. There are often hundreds and possibly even thousands of policies that control data access. There may be policies that control access by ID, or access group, by data type, or data storage system. Policies may involve clear access to the data or sometimes obfuscated or encrypted data access.
Combining access and identity information you can then determine “Who’s accessing your data now?” . This view is dynamically changing in the cloud at all times because developers, applications and cloud services continuously open up new pathways to data every day. Once you are aware of how your sensitive data (i.e. customer data) could be accessed you are halfway to preventing a cloud data breach.
After determining which identities have access to which data assets and who is accessing what, it becomes possible to understand the adversary’s mindset and gauge which pathways are most conducive to data exfiltration. (Question 4: “Do you know the vulnerable pathways through which your data could be exfiltrated?“)
Finally, understanding the combination of all the information from questions 1 to 4, provides the data necessary to answer Question #5: “Are you able to baseline authorized access versus rogue access?”. Continuous visibility of all the answers to questions 1-4 makes it possible to construct a baseline of normal data access patterns, and reveal variances and anomalies that can quickly identify and remediate unauthorized cloud data access.
Learn more:
- How Stack Identity prevents data exfiltration by managing cloud data access control
- How we help CISOs know who, what, when, where, how, and why your cloud data is being accessed right now?
- How we help cloud leaders know who is accessing your data and how to determine if your dynamic cloud environment is creating security and audit risks
- Learn how the Stack Identity breach prediction index helps answer the 5 questions to ask before cloud identity risks become data breaches